Can ransomware be identified and decrypted?
Ransomware is a particularly nasty form of malware that holds your computer’s files or entire operating system hostage until a ransom is paid (hence the name). It’s one of the most brutal and effective cyber attacks, particularly when used against businesses.
There aren’t many statistics available on how ransomware affects individuals, but one thing is certain. Ransomware affects companies on an astronomical level. Various statistics show that:
- Ransomware cost businesses more than $8 billion per year in 2018
- There was a 79% overall increase in malware-targeted businesses in 2018
- Fewer than a third of the businesses that pay the ransom retrieve all of their money
- The average cost of a ransomware attack on businesses was $133,000
- Less than one-quarter of SMBs report their ransomware attacks
- Over a quarter of all companies would pay between $20,000 and $50,000 to hackers to recover their data
- A business will fall victim to a ransomware attack every 14 seconds by 2019, and every 11 seconds by 2021
- 60% of cryptocurrency transactions can be traced back to individuals
- $51,000: the unpaid ransomware demand for the city of Atlanta, GA; $17 million: the recovery costs
Numerous cyber security organizations, media outlets, and government agencies (including the FBI) suggest that companies should simply not pay ransoms. The main arguments against paying ransomware are 1) victims don’t always receive a decryption key even after paying, and 2) that paying the ransom only encourages cyber attackers, and could lead them to target you again.
The FBI also suggests that instead of paying ransomware, you should be focused on stronger security to prevent ransomware in the first place. Security and ransomware training are easily available and highly valuable, and most companies should be putting their employees through some type of digital security training in this modern age. But while preventative measures are certainly necessary, what’s a company to do once ransomware has already struck? It’s easy to say “don’t let it happen in the first place”, but that isn’t very comforting for the thousands of companies that experience ransomware attacks every day.
Can ransomware be identified and decrypted?
That brings us to the most important question of this article. The short answer is, it depends.
There have in fact been numerous advances made in combating ransomware, including free tools for decrypting files that have been encrypted by ransomware. These efforts are being undertaken by joint efforts between security organizations, in an effort to combat ransomware that has already infected networks, and help companies recover their data without paying the ransom.
The most popular is No More Ransom, which was launched as an effort between Europol, the National High Tech Crime Unit of the Netherlands, and McAfee. Users will upload two encrypted files from their computer, along with the address where ransom payment should be sent.
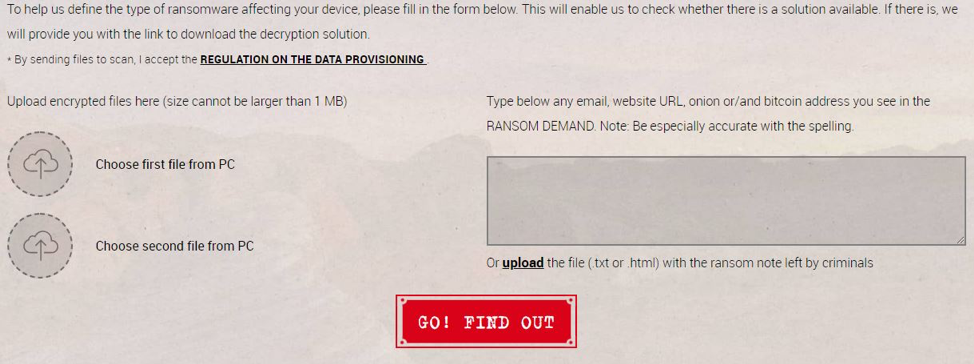
No More Ransom will then attempt to identify the specific ransomware virus, and provide the user with a tool for decrypting their files, if one is available. As of writing, there are unique decryption tools available for over 100 types of ransomware.
Many anti-virus companies also offer decryption tools for specific ransomware strains:
- Kaspersky NoRansom
- Avast Ransomware Decryption Tools
- QuickHeal
- TrendMicro Ransomware Decryptor
- McAfee Ransomware Recover
As each individual case is different, decryption tools are not a guarantee. However, many have a good success rate, and are always worth a try before anything else.
Conclusion
While it can be tempting to just pay a ransom and shrug it off as the “cost of doing business” in a digital age, it really only serves to encourage ransomware attackers. Ideally, you should have shadow backups of all files on your network, and if ever struck by ransomware, quarantine the affected computers and determine what type of ransomware.
If it is a previously unknown ransomware tool for which there is no current decryption method, perhaps allowing a security lab to investigate would be a wise course of action. It may lead to new research in cyber security, and help other companies around the world.
As always we recommend layered protection for your devices. One of our favorite products is Malwarebytes Anti-Malware.
